Overview
The Value of Frameworks for Cybersecurity
Strong cybersecurity frameworks are crucial in a time when cyber dangers are developing at a never-before-seen rate. Enterprises, no matter their importance or quarter, come across ceaseless endeavors from cyber adversaries in search of to capitalize on weaknesses. Organizations want a comprehensive cybersecurity framework as a guide to efficiently manipulate and mitigate dangers. It no longer supports simply the protection of sensitive records however additionally the upholding of patron self assurance and operational integrity.
NIST CSF 2.0 Overview
A mainstay of the cybersecurity environment for a considerable amount of time is the Cybersecurity Framework (NIST CSF) developed by using the National Institute of Standards and Technology. It has given businesses a bendy and organized method for managing and enhancing their cybersecurity posture for the reason that its original launch in 2014. The most current version, NIST CSF 2.0, is an enormous development that takes under consideration fresh perspectives and tackles current issues that corporations confront. This model emphasizes how critical it is to contain cutting-edge technologies and enhance the framework’s adaptability to various enterprise settings.
Historical Background
NIST CSF Evolution
In reaction to Executive Order 13636, which changed into issued in 2013 and requested for the development of a voluntary framework to cope with critical infrastructure cybersecurity, the NIST Cybersecurity Framework was created. The preliminary edition, which became available in 2014, quickly established itself as an essential device, offering corporations an intensive, however adaptable method for identifying, evaluating, and controlling cybersecurity threats. Iterative modifications have been pushed all through time by using remarks from distinctive stakeholders and the ever-changing nature of cyber threats. Building on this history, NIST CSF 2.0 incorporates training found out from its predecessors in addition to current cybersecurity tendencies.
Notable Deviations from Previous Editions
To address trendy cybersecurity challenges, NIST CSF 2.0 consists of a number of large changes. The inclusion of rules for modern-day technology like blockchain, Internet of Things (IoT), and artificial intelligence (AI) is one of the most noteworthy additions. Furthermore, in popularity of the developing importance of defensive personal data, this edition prioritizes privacy and records safety. Additionally, the framework has been progressed to make it less complicated for small and medium-sized organizations (SMEs) to use, making sure that agencies of all sizes can efficiently position its tips into exercise.
Fundamental Elements of NIST CSF 2.0
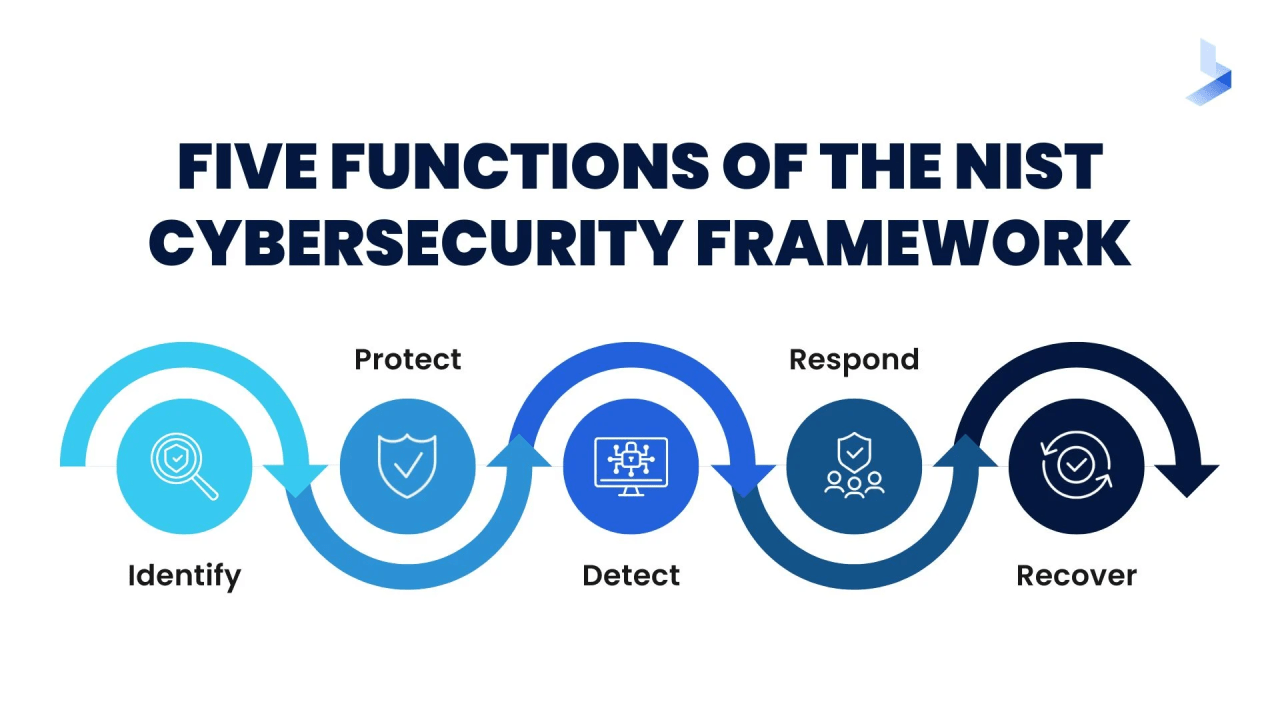
Determine
The NIST CSF’s center “Identify” feature focuses on helping corporations benefit from higher information of cybersecurity risks. This involves figuring out capacity factors of vulnerability and categorizing critical systems, information, and belongings. To create a strong safety baseline, key duties include chance checks, asset management, and governance. By including threat control techniques designed specially for new and emerging technologies, NIST CSF 2.0 improves this factor and guarantees that corporations can proactively perceive possible dangers in a quick changing context.
Preserve
The “Protect” feature describes how to protect facts and vital infrastructure in opposition to online assaults. This includes installing region safeguarding technology, teaching a group of workers individuals cybersecurity exceptional practices, and organizing access controls. By incorporating modern-day protection techniques like end-to-stop encryption and zero-accept as true with structure, NIST CSF 2.0 builds on current safeguards. By strengthening defenses, these improvements help groups in making it more difficult for cyber adversaries to breach their networks.
Identify
It’s crucial to perceive cybersecurity events quickly in an effort to reduce any harm. The “Detect” feature involves putting in region processes for ongoing remark and detection which will speedy spot uncommon activity. NIST CSF 2.0 highlights how important it is to apply AI and gadget learning for superior risk detection in order that corporations can discover and counter complicated threats extra quickly. This revised framework incorporates advanced logging and monitoring features as nicely.
React
The “Response” function is answerable for growing and sporting out the necessary actions in response to a cybersecurity occasion that has been detected. Planning for incident response, communication strategies, and effect mitigation are all blanketed on this. By adding greater thorough suggestions on incident reaction coordination and collaboration, particularly in multi-tenant systems and across many industries, NIST CSF 2.0 improves this position. The purpose of these updates is to increase standard resilience and expedite reaction activities.
Recuperate
Restoring offerings and competencies following a cybersecurity event is referred to as recovery. The “Recover” characteristic makes it positive that organizations are able to quickly recover from interruptions with the aid of highlighting the significance of continuity and resilience planning. Updated recuperation techniques that consider the information received from previous high-profile cyber disasters are supplied with the aid of NIST CSF 2.0. This offers commands on a way to use backup structures to assure facts availability and integrity, behavior put up-occasion reviews, and decorate healing strategies.
Unique Elements of NIST CSF 2.0
Incorporating New Technologies
NIST CSF 2.0’s proactive approach to integrating emerging technologies is considered one of its maximum awesome characteristics. With the growing adoption of AI, IoT, and blockchain via organizations, the framework gives precise suggestions for dealing with the particular risks related to these technologies. It affords methods, as an instance, of protective AI systems from hostile attacks and guaranteeing the accuracy of blockchain transactions. NIST CSF 2.0 ensures that companies live beforehand of the curve in cybersecurity readiness by way of addressing those modern technologies.
Increased Organizational Flexibility
Since there is nobody-length-fits-all technique to cybersecurity, NIST CSF 2.0 is built with an increased degree of flexibility. Organizations can personalize the framework’s suggestions to match their specific requirements, to have assets, and chance profiles. Small and medium-sized agencies (SMEs), who could have one-of-a-kind assets and limitations than larger corporations, will specifically benefit from this. Sector-precise policies have also been blanketed to the new framework, taking into account extra correct and green application throughout lots of agencies.
A Greater Focus on Data Protection and Privacy
NIST CSF 2.0 emphasizes statistics privateness and protection more than before in reaction to developing concerns in these regions. It offers thorough statistics on setting privateness controls in the region and is compliant with global privacy necessities inclusive of the General Data Protection Regulation (GDPR). This covers steps to reduce the quantity of statistics amassed, improve records anonymization, and assure openness in information processing approaches. NIST CSF 2.0 facilitates organizations to follow ever-tougher regulations and fosters trust by way of inclusive privacy into its primary components.
Strategies for Implementation
How to Implement NIST CSF 2.0
Using NIST CSF 2.0 calls for a few critical moves. Organizations ought to first thoroughly examine their existing cybersecurity posture and pinpoint any gaps in comparison to the framework’s suggested practices. Subsequently, they needed to layout a customized execution method, rating obligations in line with chance and accessibility of assets. This plan has to have thorough schedules, assigning of obligations, and development tracking signs. In order to guarantee that every employee is aware of their duties for preserving cybersecurity, schooling and recognition initiatives are also vital. In order to live consistent with the framework and alter to changing threats, ongoing tracking and habitual evaluations are vital.
Examples of Effective Implementations
NIST CSF has been carried out efficiently by using several organizations in numerous sectors, resulting in tremendous blessings such as advanced protection and compliance. For instance, the framework becomes utilized by a pinnacle healthcare issuer so one can secure patient facts and adhere to HIPAA guidelines. They notably reduced the variety of statistics breaches by figuring out and mitigating vital vulnerabilities by means of adhering to NIST CSF requirements. Similarly, to decorate its incident response skills and facilitate a faster and more green restoration from cyber incidents, a monetary services company made use of NIST CSF. These case studies exhibit the framework’s usefulness in numerous real-international conditions.
Typical Problems and Their Fixes
NIST CSF 2.0 implementation may be hard in a number of methods, specifically for firms with little funding or revel in. Typical barriers encompass a loss of qualified cybersecurity professionals, good finances, and organizational opposition to trade. Organizations can use a mixture of inner and outside resources to overcome those boundaries. This may want to entail developing a continuous improvement subculture, the use of automated safety solutions, and employing cybersecurity consultants. Achieving govt guidance and guaranteeing congruence with corporate dreams also are crucial for a successful deployment.
Applications Specific to Industry
Medical Care
Because affected person statistics is sensitive and policies are strict, the healthcare sector has specific cybersecurity demanding situations. NIST CSF 2.0 offers custom designed guidance to help healthcare institutions in safeguarding electronic health statistics (EHRs) and guaranteeing adherence to legal guidelines like HIPAA. Strong entry to controls ought to be installed, threat exams need to be executed on a everyday basis, and the security of medical gadgets linked to the network must be assured. Healthcare companies can enhance their cybersecurity posture and defend patient self belief through enforcing NIST CSF 2.0.
Financial Services
Because they oversee such huge quantities of treasured belongings, monetary establishments are regularly the goals of cyberattacks. Comprehensive techniques for safeguarding monetary records, spotting fraud, and dealing with emergencies are provided via NIST CSF 2.0. This includes stringent authentication techniques, sophisticated risk detection systems, and encryption of touchy facts. Financial services agencies can fortify their defenses against cyberattacks and cling to felony policies like the Payment Card Industry Data Security Standard (PCI DSS) and the Gramm-Leach-Bliley Act (GLBA) through aligning with NIST CSF 2.0.
Production
Cybersecurity is critical inside the production industry to protect highbrow belongings and hold the integrity of industrial procedures. NIST CSF 2.0 covers the specific threats that manufacturers confront, such as supply chain vulnerabilities and the safety of business control systems (ICS). Segmenting networks to separate important systems, setting strict entry to rules in location, and wearing out frequent security audits are other pointers. Manufacturers can safeguard their operations from cyber interruptions and keep their competitive edge through adhering to NIST CSF 2.0.
Administration
Because they manage so many touchy statistics, government groups are often the goal of cybercriminals seeking to reason disruptions or steal records. NIST CSF 2.0 offers specific suggestions for safeguarding citizen statistics, retaining operational continuity, and protecting government networks. This includes installing strong identity and get entry to manipulate procedures, improving incident response talents, and conserving frequent attention and training campaigns. Government agencies can improve their cybersecurity posture and keep public self belief by enforcing NIST CSF 2.0.
NIST CSF 2.0’s Function in Regulation and Compliance
NIST CSF to Other Standards Mapping
Organizations can more effortlessly gain compliance with NIST CSF 2.0 for the reason that it’s designed to be compliant with a wide variety of cybersecurity standards and laws. The framework enables the streamlining of compliance tactics for companies via imparting mappings to requirements like ISO/IEC 27001, COBIT, and the GDPR. Through the usage of these mappings, entities can assure that their cybersecurity protocols comply with numerous regulatory mandates, thereby mitigating compliance expenses and augmenting ordinary safety features.
Rewards for Adhering to Regulations
There are many benefits to the use of NIST CSF 2.0 for regulatory compliance. The framework’s adaptable approach helps companies address cybersecurity threats, including technological weaknesses and human factors. Adhering to NIST CSF 2.0 demonstrates organizations’ due diligence in addressing cybersecurity risks, a critical aspect of regulatory compliance. Furthermore, the framework’s attention on ongoing development guarantees that organizations keep to converting policies and hints.
Prospective Regulatory Patterns
Regulations are growing increasingly enormous and strict as cyber risks remain to trade. NIST CSF 2.0 provides a robust, flexible framework for managing cybersecurity risks, helping organizations stay ahead of evolving trends. Future regulations may focus on supply chain security, data privacy, and advancing technology security. Organizations can use NIST CSF 2.0 to address future challenges and ensure ongoing regulatory compliance.
Common Questions and Answers (FAQs)
1. What is NIST CSF 2.0’s primary objective?
NIST CSF 2.0’s primary objective is to give enterprises an extensive and adaptable framework for handling cybersecurity threats. It provides principles and practices to recognize, thwart, detect, respond to, and recover from cyber attacks, enhancing security and resilience.
2. What distinguishes NIST CSF 2.0 from its predecessors?
NIST CSF 2.0 provides significant improvements, such as flexibility for businesses of all sizes, standards for emerging technologies, and a focus on privacy and data security. More thorough instructions on incident response coordination and cooperation are also included, especially for situations involving many tenants and industries.
3. Can NIST CSF 2.0 be implemented by small enterprises successfully?
Yes, small businesses can successfully implement NIST CSF 2.0. The framework is scalable and flexible, allowing companies to tailor recommendations to their specific needs. NIST CSF 2.0 also offers SMEs advice to enhance security.
Key Takeaway
Benefits of NIST CSF 2.0 Summary
NIST CSF 2.0 is a flexible framework valuable for organizations, enhancing incident response, asset protection, and regulatory compliance.
The Value of Keeping Up with Innovations in Cybersecurity
It is essential to stay current with the newest developments and best practices in the rapidly evolving field of cybersecurity. NIST CSF 2.0 equips organizations to manage evolving risks by addressing recent developments and cybersecurity challenges. Organizations can maintain the efficacy and resilience of their cybersecurity procedures by adhering to frameworks such as NIST CSF 2.0.
Promoting a Cybersecurity Culture of Proactivity
Embracing NIST CSF 2.0 means implementing technical controls and fostering a proactive cybersecurity culture. This entails raising awareness, supporting ongoing development, and making sure cybersecurity is incorporated into every facet of the company. Adopting a proactive cybersecurity approach enhances defenses and builds future resilience.
This analysis of NIST CSF 2.0 highlights the importance of a systematic cybersecurity approach, framework updates, and practical implementation tactics. Organizations can enhance security, comply with legal requirements, and stay ahead of cyberthreats by using NIST CSF 2.0.